What is Entitlement ?
Entitlements refer to the specific permissions or rights granted to users or roles within a system. These permissions dictate what actions or resources a user is allowed to access or manipulate. The types of entitlements can vary depending on the system or application being used.
Take an example, here is an application example, where SalesForce has different set of permission, which is typically can be defined as Read, Create, Edit, Delete, View All, Modify All.
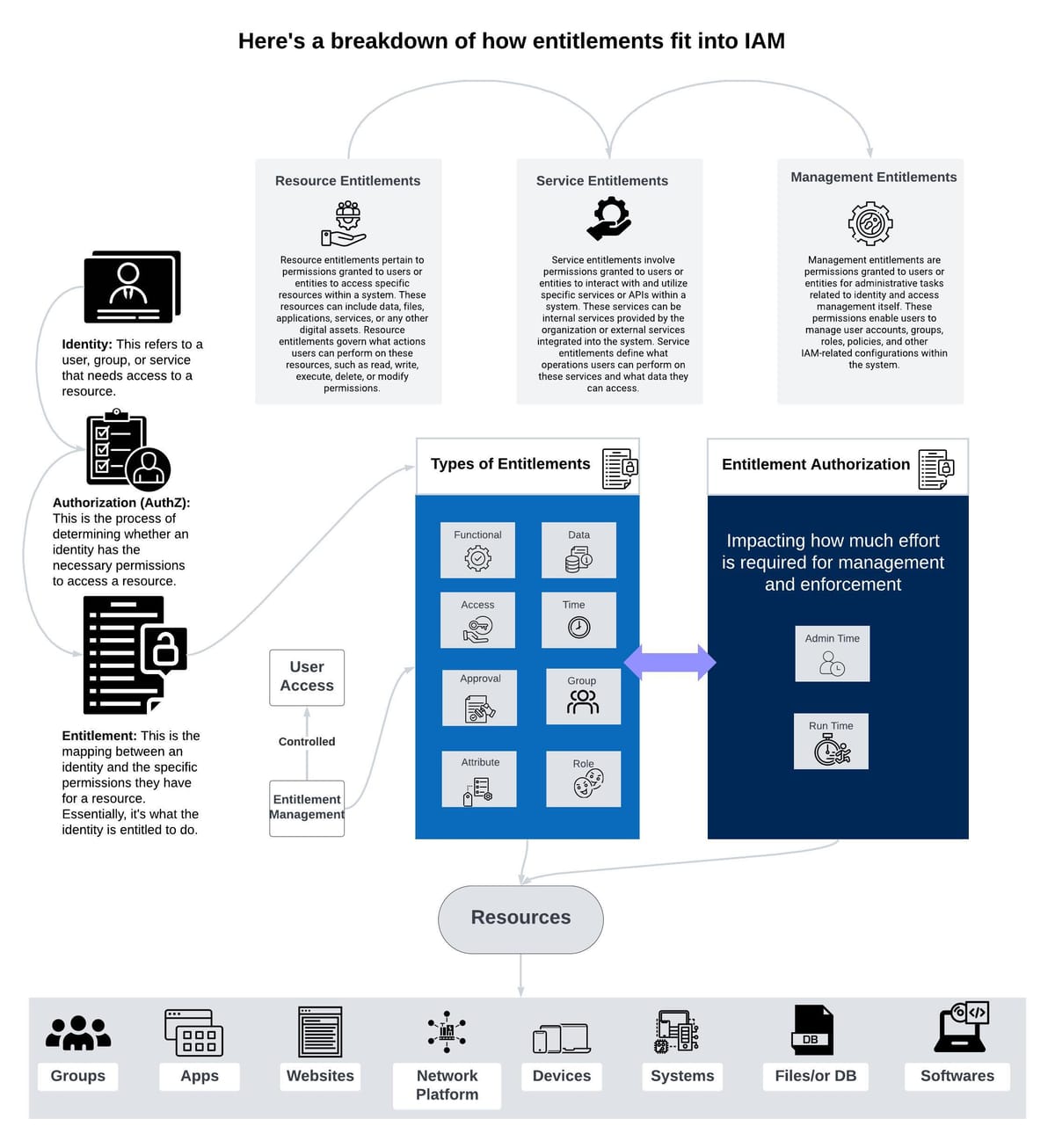
Every application has its own way of implementing permission or entitlement locally.The diagram is about how entitlements fit into Identity and Access Management (IAM). IAM is a security framework that deals with managing access to resources. Entitlements, in the context of IAM, are basically the permissions assigned to users or groups to access specific resources within a system.
The diagram breaks down entitlements into three categories:
- Resource Entitlements: These are permissions granted to users or entities to access specific resources within a system. Resources can include data, files, applications, services, or any other digital assets. Resource entitlements govern what actions users can perform on these resources, such as read, write, execute, delete, or modify permissions.
- Service Entitlements: These involve permissions granted to users or entities to interact with and utilize specific services or APIs within a system. Service entitlements define what operations users can perform on these services and what data they can access.
- Management Entitlements: These are permissions granted to users or entities for administrative tasks related to identity and access management itself. These permissions enable users to manage user accounts, groups, roles, policies, and other IAM-related configurations within the system.
The diagram also identifies the different aspects of entitlements such as:
- Identity: This refers to a user, group, or service that needs access to a resource.
- Authorization (AuthZ): This is the process of determining whether an identity has the necessary permissions to access a resource. Entitlement authorization considers factors like functional (how much effort is required for management and enforcement), data (what data is being accessed), access (what type of access is being granted - user, group, admin), time (for how long is the access granted), and impact (how granting access can impact security).
- Entitlement: This is the mapping between an identity and the specific permissions they have for a resource. Essentially, it's what the identity is entitled to do.
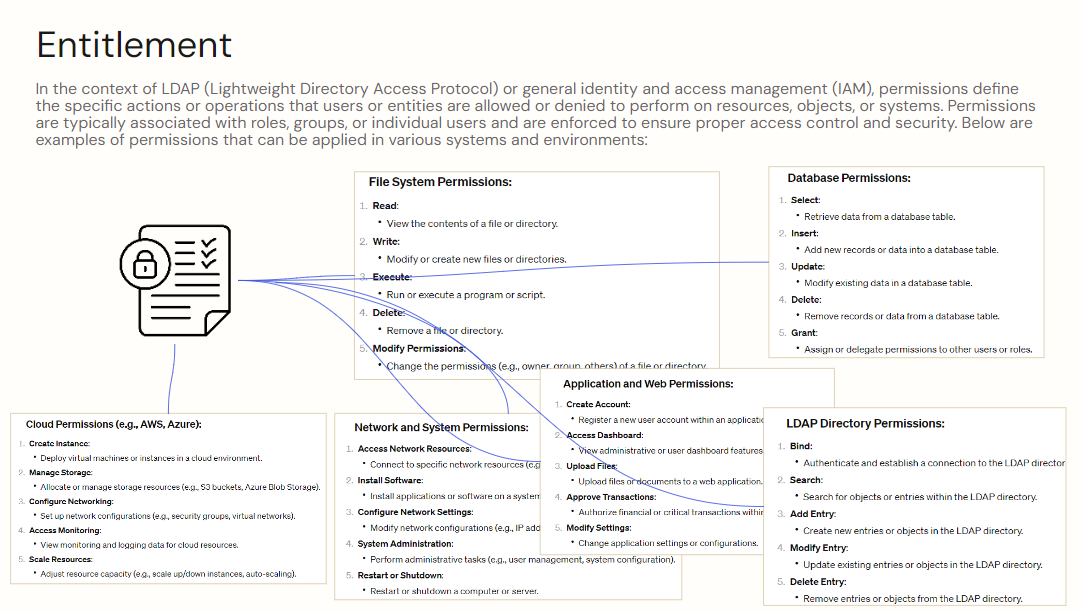
Finally, the bottom part of the diagram shows some examples of resources that entitlements can be applied to, including databases, applications, websites, network platforms, devices, systems, files, and software.
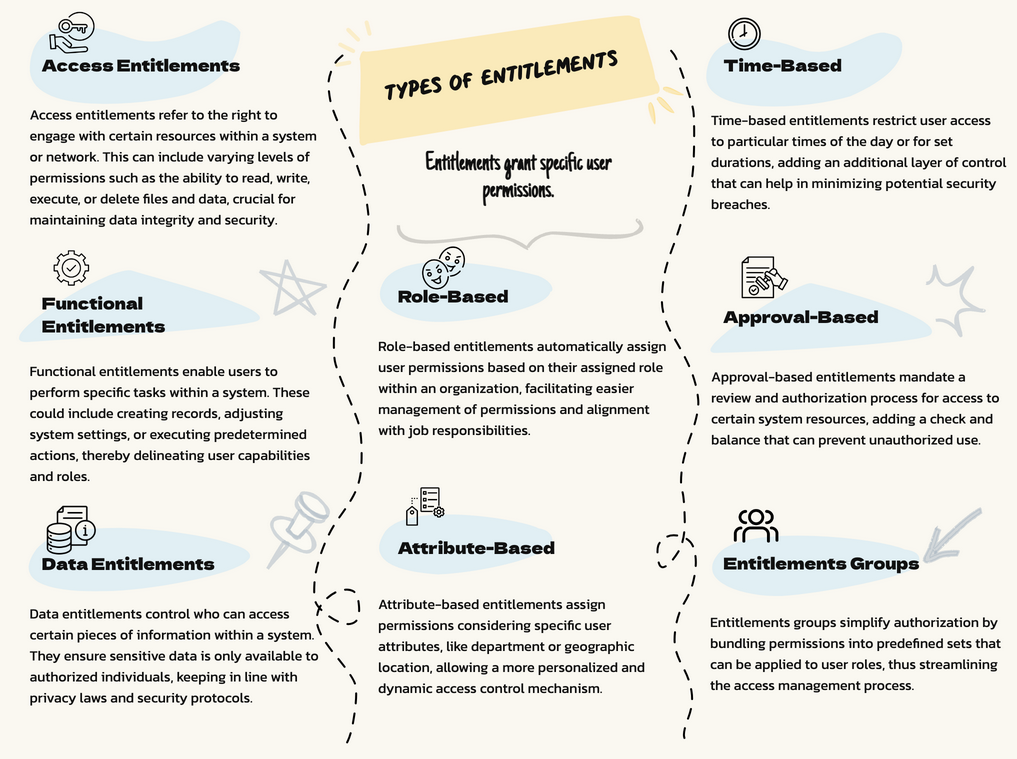
Here is the Types of Entitlements :