IGA Maturity Model
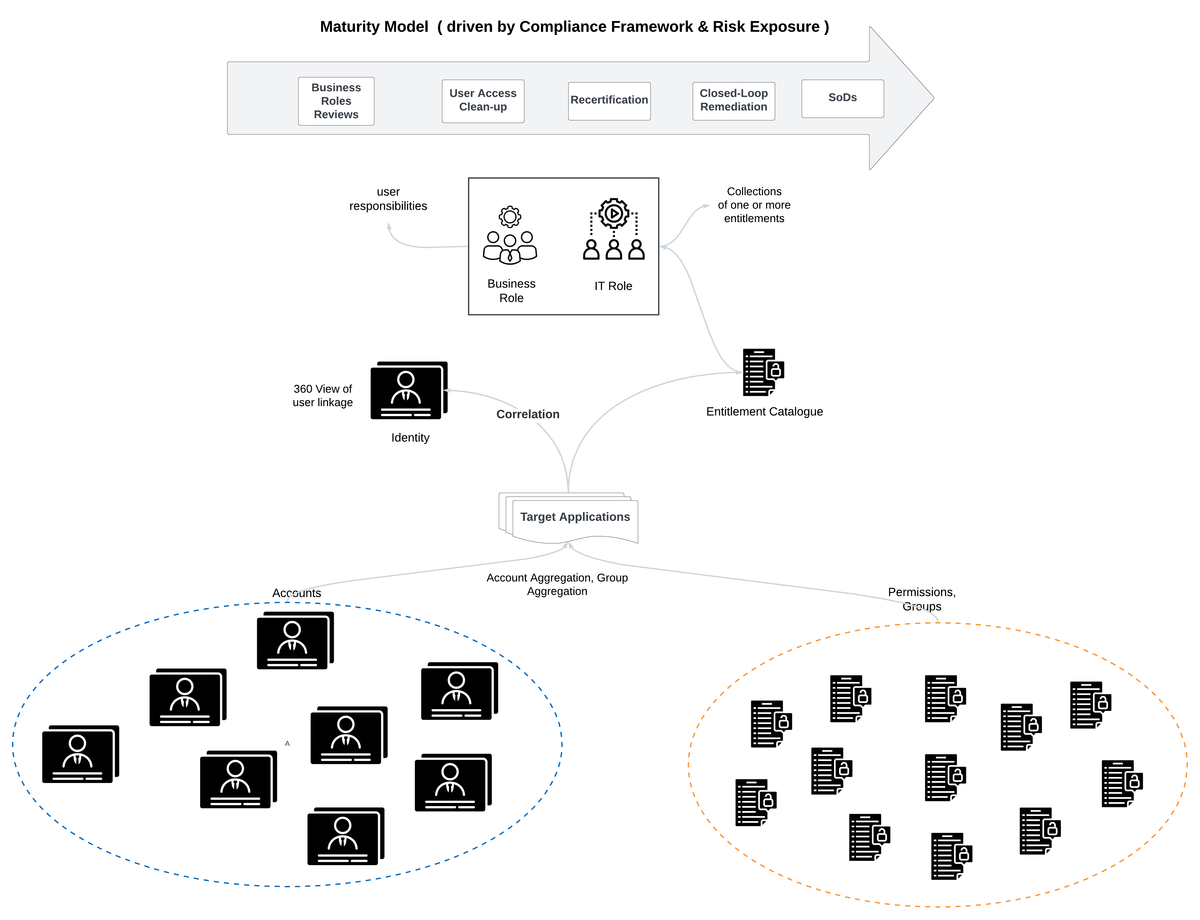
One of the challenge that we face when implementing IGA tools like Sailpoint and Saviynt is to showcase values to the stakeholders, and I have seen the struggle to explain that it takes a while to move the needle and start generating the value to justify the ROI.
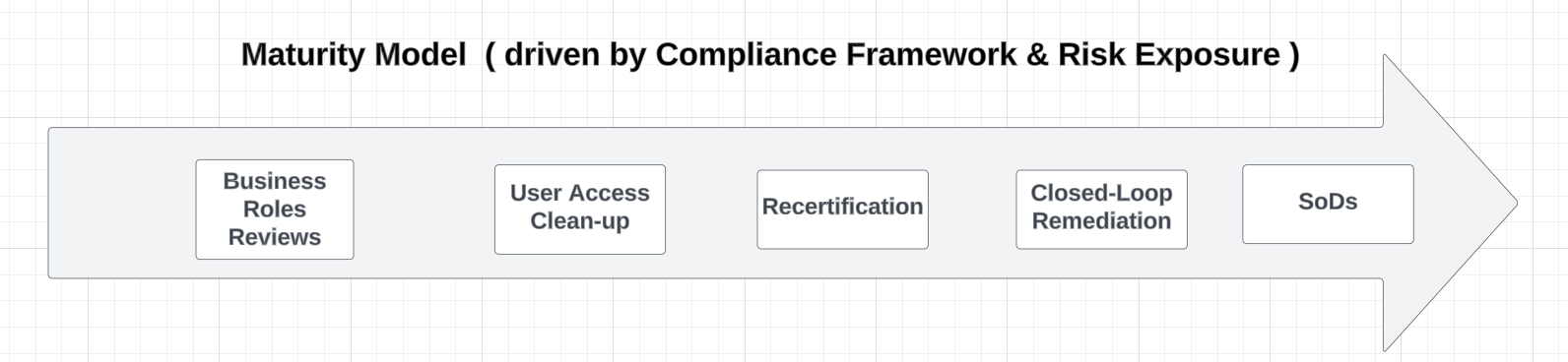
Most of the value is aligned with maturity level :
Different levels of maturity, such as:
- Initial: The organization is just starting to think about IAM.
- Ad hoc: The organization has some IAM processes in place, but they are not well-defined or enforced.
- Defined: The organization has documented IAM processes.
- Optimized: The organization has automated IAM processes.
Various components which can drive the maturity level :
The IGA (Identity Governance and Administration) Maturity Model is a framework used to assess and advance an organization's capability in managing identity and access governance effectively. This model helps organizations understand where they stand in terms of identity governance maturity and provides a roadmap for improvement. The maturity model typically consists of several stages or levels, each representing a different level of maturity in identity governance practices.
Here is a general outline of what an IGA Maturity Model might look like:
- Initial Stage/Level 1: Ad Hoc
- Identity governance processes are manual and decentralized.
- Limited visibility and control over user access and entitlements.
- Reactive approach to identity and access management issues.
- Basic compliance with regulatory requirements.
- Managed Stage/Level 2: Defined
- Basic identity management processes and controls are established.
- Some automation of identity lifecycle management (provisioning, deprovisioning).
- Basic role-based access controls (RBAC) implemented.
- Compliance-driven focus with periodic audits.
- Defined Stage/Level 3: Managed
- Formal identity governance program established with defined policies and procedures.
- Centralized identity repository (Identity Warehouse).
- Automated provisioning and deprovisioning workflows.
- Implementation of RBAC and periodic access reviews.
- Compliance reporting and audit trails for access.
- Integrated Stage/Level 4: Optimised
- Integration of identity governance with broader IT and security systems.
- Advanced RBAC and attribute-based access controls (ABAC) implemented.
- Continuous monitoring and enforcement of access policies.
- Self-service access requests and approvals.
- Risk-based access controls and analytics for identity governance.
- Optimized Stage/Level 5: Predictive
- Mature identity analytics and intelligence capabilities.
- Predictive and adaptive access controls based on behavior analytics.
- Continuous compliance monitoring and reporting.
- Automated remediation of identity and access risks.
- Full integration with IT service management and security incident response.
Each stage represents an evolution in an organization's identity governance maturity, moving from ad hoc and reactive practices to proactive, integrated, and optimized identity governance processes.
The goal of adopting an IGA Maturity Model is to continuously improve identity and access management capabilities to meet business needs, regulatory requirements, and security objectives effectively. Organizations can use this model to assess their current state, identify gaps, prioritize improvements, and track progress towards higher maturity levels in identity governance and administration.