IAM Pillars
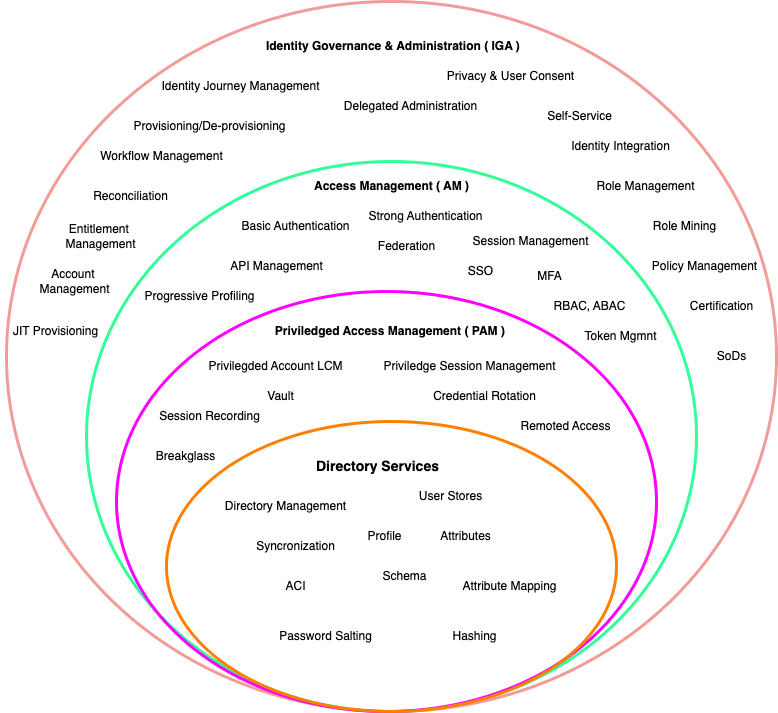
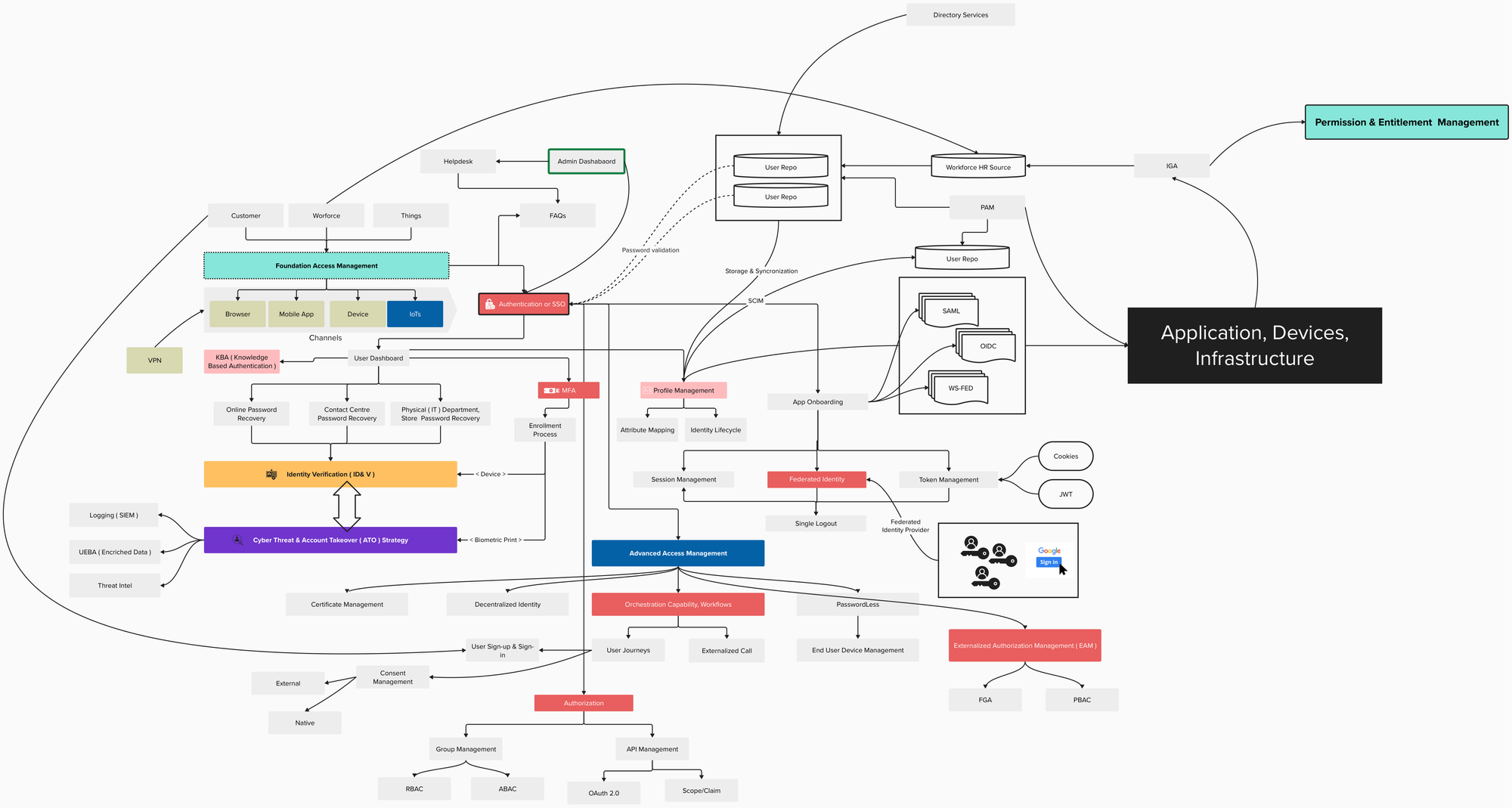
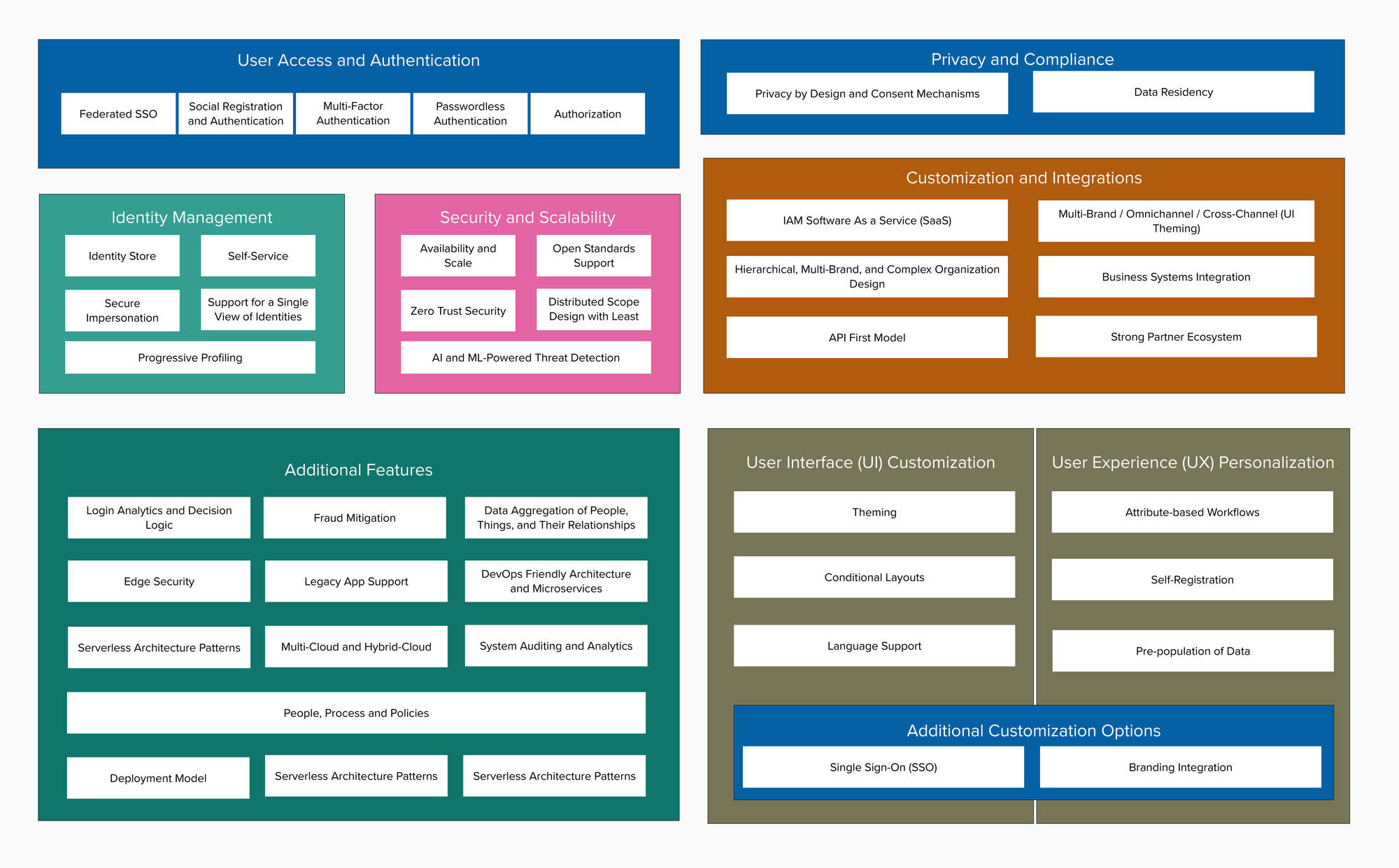
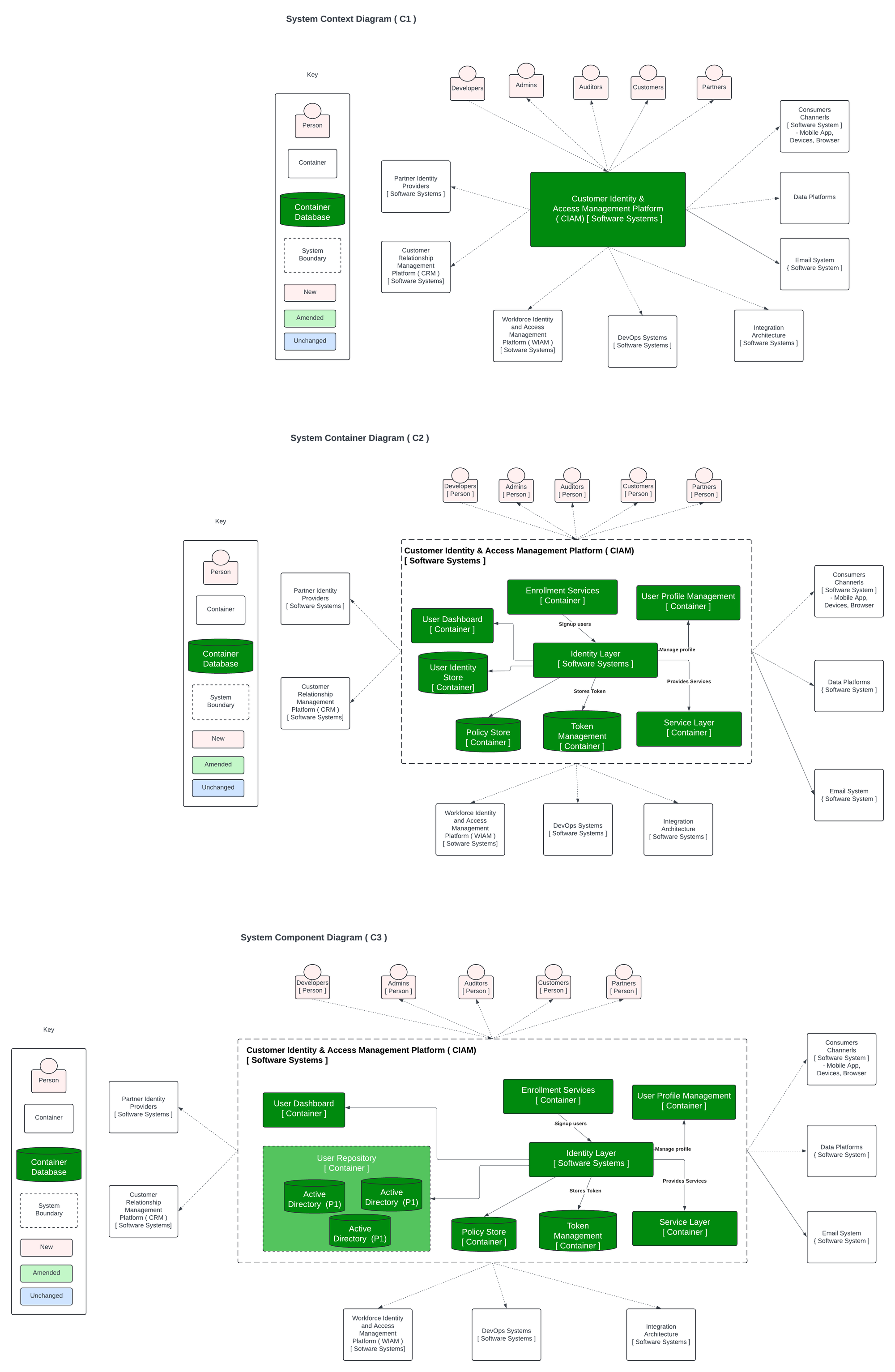
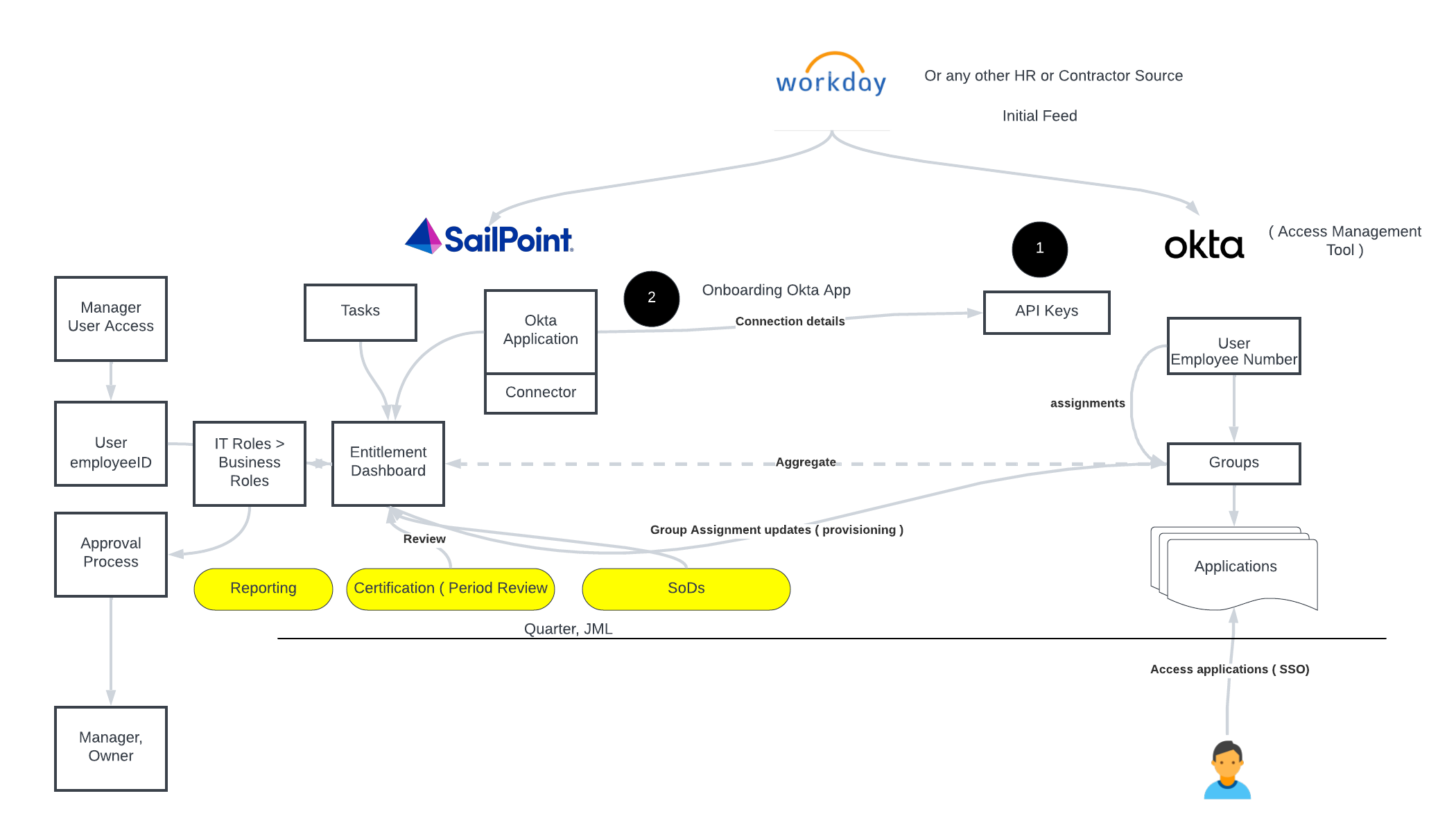
🔒 Embracing the Pillars of IAM: Directory Services, PAM, AM, and IGA
🔒In today's digital landscape, securing access to critical resources is paramount. As businesses navigate complex security challenges, it's crucial to establish a robust Identity and Access Management (IAM) framework.
Let's delve into four fundamental pillars that constitute IAM:
1️⃣ Directory Services: At the heart of IAM, directory services provide a centralized repository for user identities and access privileges. Whether it's Active Directory, LDAP, or modern cloud-based solutions like Azure AD, directory services streamline user management, authentication, and authorization processes.
2️⃣ Privileged Access Management (PAM): Safeguarding privileged accounts is non-negotiable. PAM solutions offer granular control over who can access sensitive systems, applications, and data. By enforcing strict authentication measures, session monitoring, and just-in-time access, PAM mitigates the risk of insider threats and unauthorized access to critical assets.
3️⃣ Authentication Management (AM): In the age of multifactor authentication (MFA) and biometric security, AM plays a pivotal role in verifying user identities. From traditional passwords to cutting-edge authentication methods like facial recognition and fingerprint scanning, AM solutions bolster security while ensuring a frictionless user experience.
4️⃣ Identity Governance and Administration (IGA): Maintaining compliance and enforcing access policies across the organization requires robust IGA capabilities. By automating user provisioning, deprovisioning, and access certifications, IGA solutions empower businesses to govern identities effectively, mitigate risks, and streamline audit processes.As organizations embrace digital transformation, the synergy between these IAM pillars becomes increasingly critical. By integrating Directory Services, PAM, AM, and IGA into a cohesive IAM strategy, businesses can fortify their defenses, protect sensitive data, and foster a culture of security and compliance.