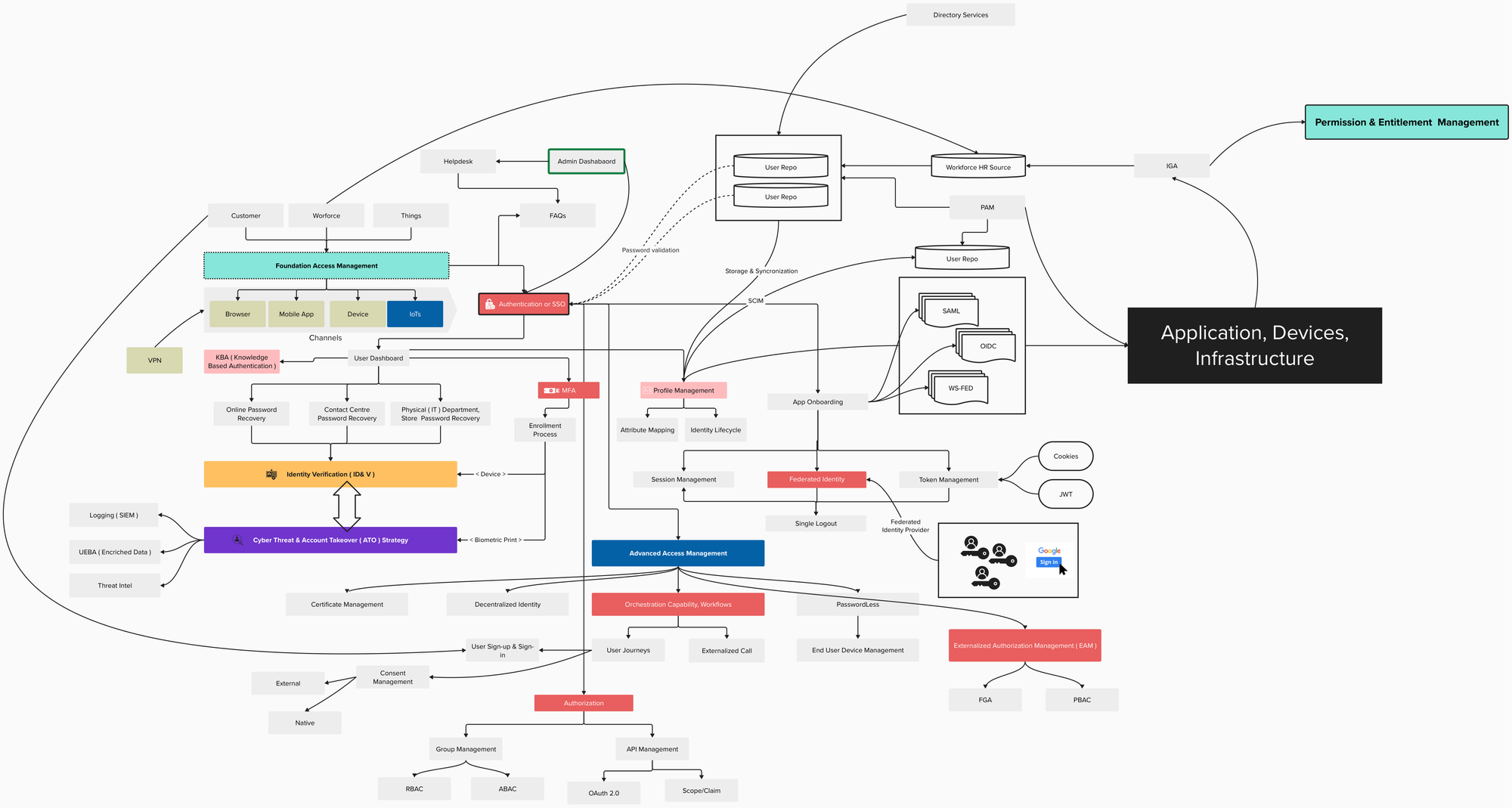
Authentication in the context of Digital Identity
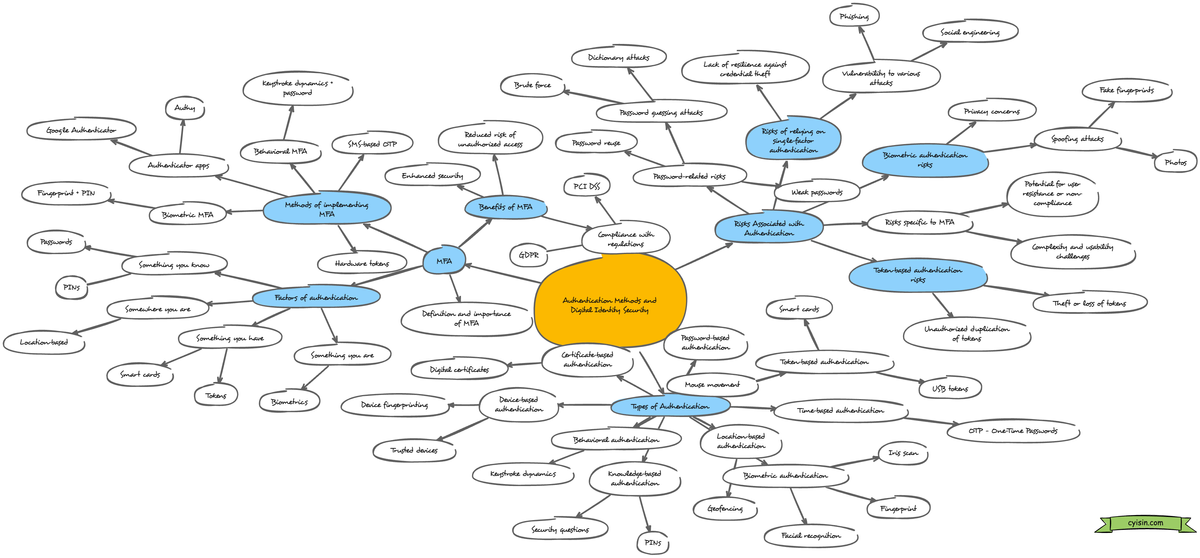
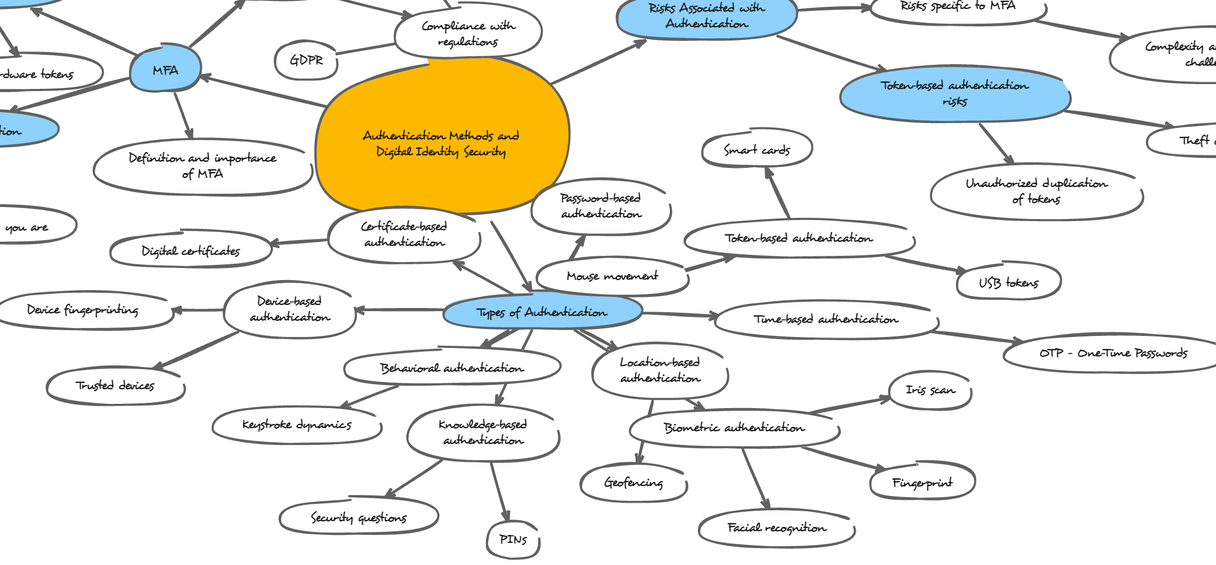
Types of Authentication:
Here's a breakdown of the different authentication methods you mentioned:
- Password-based authentication: This is the most common method, using a username and password combination. It's convenient but vulnerable to breaches if passwords are weak or reused.
- Biometric authentication (fingerprint, facial recognition, iris scan): This verifies your identity through unique physical characteristics. It's secure, but can be fooled by spoofing in some cases and raises privacy concerns.
- Token-based authentication (smart cards, USB tokens): Uses a physical token that generates a code or stores cryptographic information for authentication. It adds security but can be lost or stolen.
- Knowledge-based authentication (security questions, PINs): Relies on answering secret questions or using a Personal Identification Number (PIN). It's convenient but not very secure if questions are easily guessable or PINs are weak.
- Location-based authentication (geofencing): Uses your device's location to verify if you're within a designated area for access. This adds a layer of security for location-sensitive applications but relies on accurate location services.
- Time-based authentication (OTP - One-Time Passwords): Generates a unique code that expires after a short time, typically sent via SMS or generated by an app. It adds security but can be inconvenient if relying on SMS or if the app isn't readily available.
- Behavioral authentication (keystroke dynamics, mouse movement): Analyzes typing patterns or mouse movements to identify users based on their unique behavior. It's not widely used yet but can be an additional security layer.
- Certificate-based authentication (digital certificates): Uses digital certificates to verify the identity of both the user and the server they're connecting to. This is common for secure communication channels but requires certificate management.
- Device-based authentication (device fingerprinting, trusted devices): Identifies and verifies a user based on their device's unique characteristics. This can be helpful in conjunction with other methods but can be bypassed if a user accesses from a different device.
Multi-Factor Authentication (MFA):
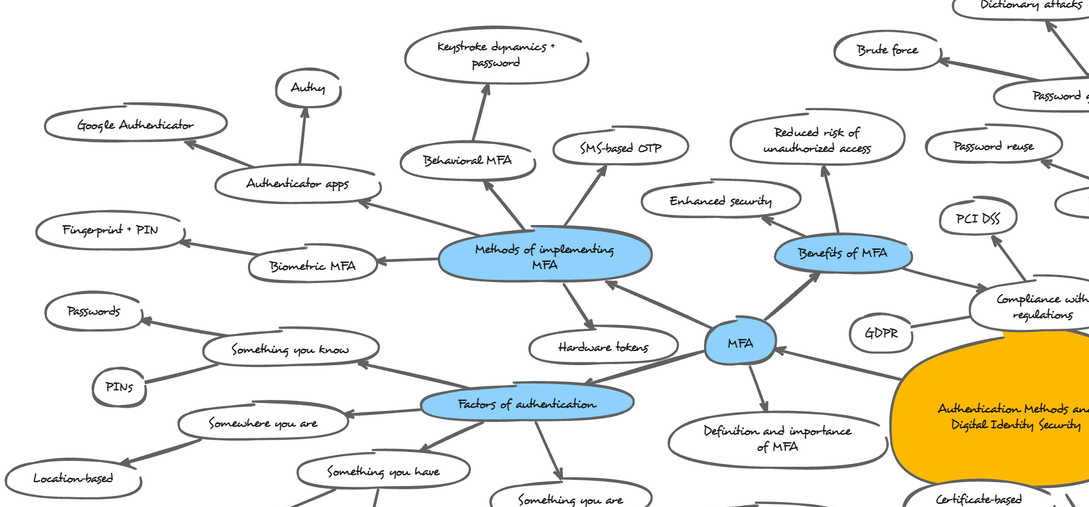
Definition: MFA is a security measure that requires two or more of the authentication factors mentioned above. This significantly increases the difficulty for unauthorized access even if an attacker obtains one factor (e.g., password).
Importance: MFA is crucial for protecting sensitive information and accounts. It adds layers of security, making it much harder for attackers to gain access.
Factors of Authentication: These are the different categories of factors used in MFA:
- Something you know (passwords, PINs)
- Something you have (tokens, smart cards)
- Something you are (biometrics)
- Somewhere you are (location-based)
Methods of Implementing MFA:
Here are some common ways to implement MFA:
- SMS-based OTP: A one-time code is sent via SMS for verification. It's convenient but vulnerable if the attacker gains control of the phone number.
- Authenticator apps (Google Authenticator, Authy): These apps generate codes on your smartphone for verification. More secure than SMS but requires user to have the phone readily available.
- Hardware tokens: Physical tokens that generate codes or store cryptographic information for verification. Most secure option but can be lost or stolen.
- Biometric MFA (fingerprint + PIN): Combines fingerprint scan with a PIN for verification. Offers good security and convenience.
- Behavioral MFA (keystroke dynamics + password): Combines analyzing typing patterns with a password for verification. Less common but can be an additional layer.
Benefits of MFA:
- Enhanced security: Adds significant layers of protection against unauthorized access.
- Reduced risk of unauthorized access: Makes it much harder for attackers to bypass security measures.
- Compliance with regulations: Many regulations (e.g., GDPR, PCI DSS) require strong authentication for protecting sensitive data.
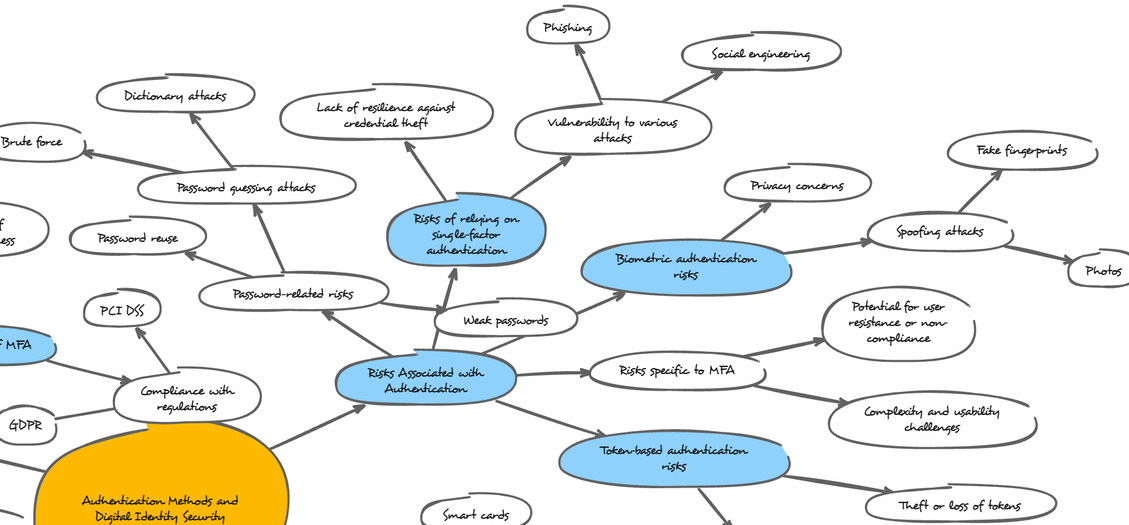
Risks Associated with Authentication:
Here are some of the risks associated with different authentication methods:
Password-related risks:
- Weak passwords: Easily guessed or cracked by attackers.
- Password reuse: Using the same password for multiple accounts increases risk if one is compromised.
- Password guessing attacks (brute force, dictionary attacks): Attackers try to guess passwords using automated methods.
Biometric authentication risks:
- Spoofing attacks: Using fake fingerprints, photos, or other methods to bypass biometric scanners.
- Privacy concerns: Collection and storage of biometric data raises privacy concerns.
Token-based authentication risks:
- Theft or loss of tokens: Compromises the security if a token falls into the wrong hands.
- Unauthorized duplication of tokens: In some cases, tokens might be vulnerable to copying